Conquering 5 Crucial Cybersecurity Threats: Ultimate Defense Strategies
Conquering 5 Crucial Cybersecurity Threats: Ultimate Defense Strategies
Related Articles: Conquering 5 Crucial Cybersecurity Threats: Ultimate Defense Strategies
- Amazing Breakthroughs: 5 Revolutionary Green Tech Solutions Transforming Our Planet
- 7 Amazing Smart Cities Revolutionizing Urban Life
- Cloud Computing: Myths Vs. Reality
- Amazing Breakthroughs: 5 Key Advances Shaping The Future Of Space Technology
- Astonishing Quantum Leap: 5 Key Breakthroughs Revolutionizing Computing
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Conquering 5 Crucial Cybersecurity Threats: Ultimate Defense Strategies. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Conquering 5 Crucial Cybersecurity Threats: Ultimate Defense Strategies
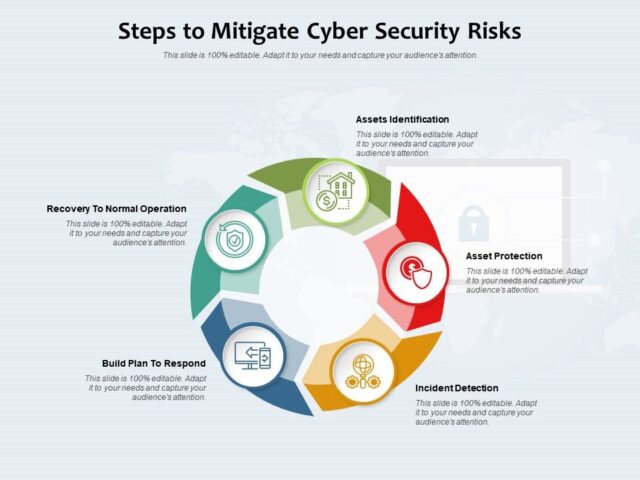
The digital landscape is a battlefield. Every day, businesses and individuals alike face a relentless barrage of cyberattacks, ranging from minor annoyances to catastrophic data breaches. The sheer volume and sophistication of these threats make it crucial to understand the most prevalent dangers and implement robust defensive measures. This article will delve into five crucial cybersecurity threats, analyzing their mechanisms and providing practical solutions to bolster your digital defenses. Ignoring these threats is not an option; the potential consequences are too severe.
1. Phishing and Social Engineering: The Human Element
Phishing remains one of the most prevalent and successful cyberattacks. It leverages human psychology to trick individuals into revealing sensitive information, such as usernames, passwords, credit card details, and social security numbers. These attacks often come disguised as legitimate emails, text messages, or website links, mimicking trusted institutions like banks, government agencies, or online retailers. Sophisticated phishing campaigns may even involve personalized emails, crafted to appear authentic and tailored to the recipient.
Mechanisms:
- Spear phishing: Targets specific individuals or organizations with highly personalized messages.
- Whaling: Targets high-profile individuals, such as CEOs or executives, to gain access to sensitive corporate data.
- Clone phishing: Duplicates legitimate emails to trick recipients into clicking malicious links.
- Smishing: Phishing attacks conducted via SMS messages.
- Vishing: Phishing attacks conducted via voice calls.
Solutions:
- Security Awareness Training: Educating employees about phishing tactics is paramount. Regular training sessions, simulations, and phishing awareness campaigns can significantly reduce the success rate of these attacks.
- Email Filtering and Authentication: Implement robust email filtering systems that detect and block suspicious emails based on sender reputation, content analysis, and other heuristics. Utilize email authentication protocols like SPF, DKIM, and DMARC to verify the authenticity of emails.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of authentication, making it significantly harder for attackers to gain access even if they obtain a password.
- URL Scanning: Before clicking on any link, use a URL scanner to check its legitimacy. Many free tools are available online.
- Suspicious Email Reporting Mechanism: Establish a clear process for employees to report suspicious emails.

2. Malware Infections: The Silent Threat
Malware encompasses a broad range of malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. This includes viruses, worms, Trojans, ransomware, spyware, and adware. Malware can be spread through various means, including malicious websites, infected email attachments, and compromised software.
Mechanisms:
- Drive-by downloads: Malware automatically downloaded to a user’s computer simply by visiting a compromised website.
- Exploiting software vulnerabilities: Malware leverages known vulnerabilities in software applications to gain unauthorized access.
- Malicious attachments: Opening infected email attachments can install malware on a computer.
- Social engineering: Tricking users into installing malware by disguising it as legitimate software.

Solutions:
- Antivirus and Anti-malware Software: Install and regularly update robust antivirus and anti-malware software on all devices. Ensure that the software includes real-time protection and automatic updates.
- Software Patching: Regularly update all software applications and operating systems to patch known vulnerabilities.
- Firewall Protection: Use a firewall to block unauthorized access to your computer system.
- Regular System Scans: Perform regular system scans to detect and remove any malware infections.
- Data Backup: Regularly back up important data to an external storage device or cloud service to mitigate the impact of ransomware attacks.
3. Ransomware Attacks: The Data Extortion
Ransomware is a particularly insidious type of malware that encrypts a victim’s data, rendering it inaccessible. Attackers then demand a ransom payment in exchange for the decryption key. The sophistication of ransomware attacks has increased significantly, with some strains targeting entire networks and demanding exorbitant sums.
Mechanisms:
- Exploiting software vulnerabilities: Ransomware can exploit known vulnerabilities to gain access to a system.
- Phishing: Ransomware can be delivered through phishing emails containing malicious attachments or links.
- Drive-by downloads: Visiting compromised websites can automatically download ransomware.
- Software supply chain attacks: Compromising the software development process to inject ransomware into legitimate software.
Solutions:
- Regular Data Backups: The most effective defense against ransomware is regular data backups. Store backups offline or in a cloud service that is separate from the main system.
- Network Segmentation: Segmenting the network can limit the impact of a ransomware attack by preventing it from spreading to other parts of the network.
- Security Awareness Training: Educating users about the dangers of ransomware and phishing attacks is crucial.
- Robust Endpoint Detection and Response (EDR): EDR solutions can detect and respond to ransomware attacks in real time.
- Incident Response Plan: Develop and regularly test an incident response plan to effectively manage a ransomware attack.
4. Denial-of-Service (DoS) Attacks: The Overload
DoS attacks aim to disrupt online services by flooding them with traffic, making them unavailable to legitimate users. Distributed Denial-of-Service (DDoS) attacks involve multiple compromised systems, amplifying the attack’s impact. These attacks can target websites, online services, and even entire networks, causing significant financial and reputational damage.
Mechanisms:
- Flooding the target with traffic: Overwhelming the target’s resources, making it unable to respond to legitimate requests.
- Exploiting vulnerabilities: Some DoS attacks exploit specific vulnerabilities in the target system.
- Botnets: DDoS attacks often leverage botnets, networks of compromised computers controlled by attackers.
Solutions:
- Web Application Firewall (WAF): A WAF can filter malicious traffic and protect against common web application attacks, including DoS attacks.
- Content Delivery Network (CDN): A CDN distributes website traffic across multiple servers, making it more resilient to DoS attacks.
- Rate Limiting: Implementing rate limiting can restrict the number of requests from a single IP address, preventing DoS attacks.
- Network Monitoring: Monitoring network traffic can help detect and respond to DoS attacks early on.
- Incident Response Plan: Having a well-defined incident response plan is crucial for effectively mitigating the impact of a DoS attack.
5. Insider Threats: The Human Factor within
Insider threats pose a significant risk, as they involve malicious or negligent actions by individuals within an organization. These threats can range from accidental data leaks to deliberate sabotage or theft of sensitive information. Employees, contractors, and even former employees can pose an insider threat.
Mechanisms:
- Accidental data leaks: Employees inadvertently sharing sensitive information with unauthorized individuals.
- Malicious insiders: Employees intentionally stealing or damaging data for personal gain or malicious purposes.
- Negligence: Employees failing to follow security policies and procedures, leading to vulnerabilities.
- Compromised accounts: Employee accounts being compromised by attackers.
Solutions:
- Strong Access Control Policies: Implement strict access control policies that limit access to sensitive data based on the principle of least privilege.
- Employee Background Checks: Conduct thorough background checks on employees, especially those with access to sensitive data.
- Security Awareness Training: Educate employees about security policies and procedures, emphasizing the importance of data protection.
- Data Loss Prevention (DLP) Tools: Implement DLP tools to monitor and prevent sensitive data from leaving the organization’s network.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
- Employee Monitoring (with proper legal and ethical considerations): Monitor employee activity, but always within legal and ethical boundaries, to detect suspicious behavior.
In conclusion, the ever-evolving landscape of cybersecurity threats necessitates a proactive and multi-layered approach to security. By understanding the mechanisms of these crucial threats and implementing the solutions outlined above, organizations and individuals can significantly enhance their digital defenses and mitigate the risks associated with cyberattacks. Remember, security is an ongoing process, not a one-time fix. Regular updates, vigilant monitoring, and continuous improvement are essential for staying ahead of the curve in the fight against cybercrime.
Closure
Thus, we hope this article has provided valuable insights into Conquering 5 Crucial Cybersecurity Threats: Ultimate Defense Strategies. We thank you for taking the time to read this article. See you in our next article!
google.com