Critical Cybersecurity Threats: 5 Powerful Trends to Master
Related Articles: Critical Cybersecurity Threats: 5 Powerful Trends to Master
- Revolutionary Smart Fabrics: 5 Key Innovations Transforming Textiles
- Revolutionary 5 Ways Sustainable Materials Transform Tech Manufacturing
- Revolutionary Leap: 5 Key Aspects Of The Autonomous Retail Store Revolution
- Revolutionary 500-Mile Range: Electric Vehicle Battery Breakthroughs
- Amazing Breakthrough: 5 Revolutionary Augmented Reality Gaming Innovations
Introduction
With great pleasure, we will explore the intriguing topic related to Critical Cybersecurity Threats: 5 Powerful Trends to Master. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Critical Cybersecurity Threats: 5 Powerful Trends to Master
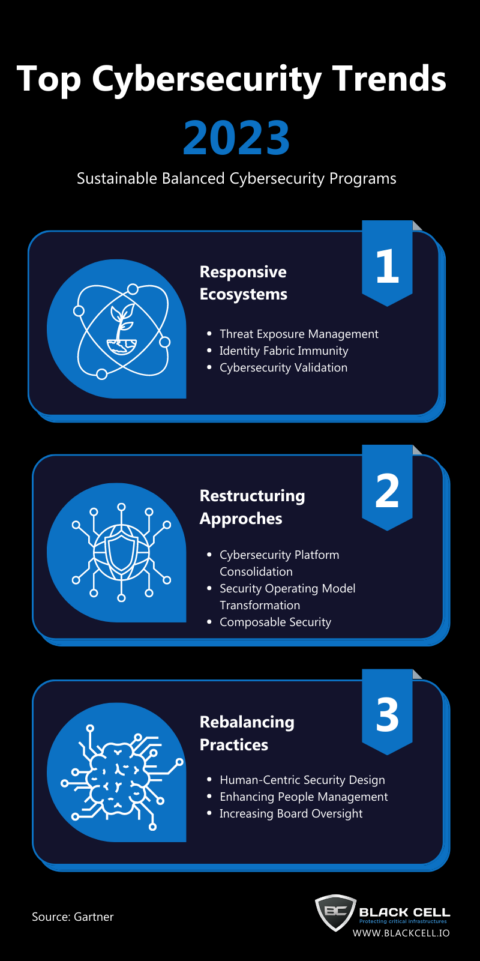
The digital landscape is a battlefield, a constant clash between innovation and malicious intent. Cybersecurity is no longer a niche concern; it’s the bedrock of modern existence, impacting everything from personal finances to national infrastructure. While advancements in technology offer unprecedented opportunities, they also present exponentially more avenues for attack. Understanding the evolving threat landscape is paramount, and failing to adapt to emerging trends leaves organizations and individuals vulnerable to devastating consequences. This article delves into five critical cybersecurity trends demanding immediate attention and proactive mitigation strategies.
1. The Rise of AI-Powered Attacks and Defenses:
Artificial intelligence (AI) is revolutionizing multiple industries, and cybersecurity is no exception. While AI offers powerful defensive capabilities, it’s also becoming a potent weapon in the hands of malicious actors. AI-powered attacks are characterized by their sophistication, scale, and speed. Traditional security measures often struggle to keep pace.
-
Sophisticated Phishing and Social Engineering: AI can analyze vast datasets of personal information to craft highly personalized phishing emails and social engineering attacks. These attacks are significantly more effective than generic phishing attempts, as they exploit individual vulnerabilities and psychological biases with unnerving accuracy. AI can even generate realistic voice clones to impersonate individuals convincingly, making voice phishing (vishing) a growing threat.
-
Automated Vulnerability Scanning and Exploitation: AI-powered tools can rapidly scan systems for vulnerabilities and automatically exploit them, bypassing traditional security controls. This automated approach allows attackers to launch attacks at scale and with unprecedented speed, significantly reducing the time window for detection and response. The ability to adapt and learn from previous attempts makes these attacks particularly challenging to defend against.
-
Advanced Malware and Evasion Techniques: AI can be used to create highly evasive malware that can adapt to changing security environments and bypass detection mechanisms. This adaptive malware can morph its code, making it difficult to identify and remove. Furthermore, AI can be employed to generate increasingly realistic malware signatures, making it challenging for antivirus software to accurately identify threats.

On the defensive side, AI is proving to be an invaluable tool. AI-powered security systems can analyze massive amounts of data to identify anomalies and potential threats in real time. Machine learning algorithms can detect patterns indicative of malicious activity that would be missed by traditional rule-based systems. AI can also automate incident response processes, speeding up the time it takes to contain and remediate security breaches. However, the development and deployment of effective AI-powered defenses require significant investment in expertise and infrastructure.
2. The Expanding Threat Landscape of IoT Devices:
The Internet of Things (IoT) has dramatically expanded the attack surface for cybercriminals. The sheer number of interconnected devices – from smart home appliances to industrial control systems – creates a vast network of potential vulnerabilities. Many IoT devices lack robust security features, making them easy targets for exploitation.
-
Lack of Security Updates and Patches: Many IoT devices receive limited or no security updates, leaving them vulnerable to known exploits. This is often due to the high cost and complexity of updating firmware on large numbers of devices. Furthermore, the lifespan of many IoT devices is relatively short, meaning that they may be left vulnerable for extended periods.
-
Weak Authentication and Encryption: Many IoT devices use weak or default passwords and lack strong encryption protocols, making them easy to access and control remotely. This allows attackers to gain unauthorized access to sensitive data or disrupt the functionality of critical systems.
-
Data Breaches and Privacy Violations: IoT devices often collect and transmit large amounts of personal data, creating significant privacy risks. Data breaches involving IoT devices can expose sensitive information such as location data, health information, and financial data.

Mitigating the risks associated with IoT devices requires a multi-faceted approach. This includes developing and implementing stronger security standards for IoT devices, ensuring that devices receive regular security updates, and promoting secure configurations and user practices. Organizations need to implement robust security policies and procedures to manage the risks associated with IoT devices within their network.
3. The Growing Sophistication of Ransomware Attacks:
Ransomware attacks continue to evolve, becoming more sophisticated and damaging. Attackers are increasingly targeting critical infrastructure, healthcare systems, and other organizations with significant impact. The consequences of a successful ransomware attack can be devastating, leading to data loss, operational disruption, financial losses, and reputational damage.
-
Double Extortion and Data Leaks: Attackers are increasingly using a "double extortion" tactic, encrypting data and threatening to leak sensitive information publicly if the ransom is not paid. This tactic significantly increases the pressure on victims to comply, as the reputational damage from a data leak can be far-reaching.
-
Targeted Attacks and Advanced Evasion Techniques: Attackers are increasingly targeting specific organizations with tailored attacks, exploiting known vulnerabilities and using advanced evasion techniques to bypass security controls. This requires a highly sophisticated understanding of the target’s systems and security posture.
-
Ransomware-as-a-Service (RaaS): The rise of RaaS has made it easier for less technically skilled individuals to launch ransomware attacks. This lowers the barrier to entry for cybercriminals, leading to a significant increase in the number of ransomware attacks.
To combat the growing threat of ransomware, organizations need to implement robust security measures, including regular backups, strong endpoint protection, employee training, and incident response plans. Furthermore, a proactive approach to threat intelligence and vulnerability management is crucial for preventing ransomware attacks.
4. The Persistence of Supply Chain Attacks:
Supply chain attacks target the vulnerabilities in an organization’s supply chain, compromising third-party vendors or software suppliers to gain access to the target organization’s systems. These attacks are particularly dangerous because they often go undetected for extended periods, allowing attackers to establish a foothold within the network before launching their main attack.
-
Compromised Software and Updates: Attackers can compromise software updates or supply chain components to distribute malware to a large number of organizations. This allows them to achieve widespread infection with minimal effort.
-
Third-Party Vendor Vulnerabilities: Many organizations rely on third-party vendors for various services and software. If these vendors are compromised, attackers can gain access to the organization’s systems through the compromised vendor.
-
Lack of Visibility and Control: Organizations often lack visibility into their entire supply chain, making it difficult to identify and mitigate risks associated with third-party vendors.
Protecting against supply chain attacks requires a multi-layered approach, including thorough due diligence of third-party vendors, robust security controls throughout the supply chain, and continuous monitoring of the supply chain for potential threats. Investing in a strong security information and event management (SIEM) system can provide the necessary visibility into the organization’s network and detect suspicious activity related to supply chain attacks.
5. The Human Element Remains Critical:
Despite technological advancements, the human element remains the weakest link in cybersecurity. Human error, negligence, and social engineering attacks continue to be major contributors to security breaches. Phishing scams, social engineering tactics, and accidental data leaks pose significant risks.
-
Phishing and Social Engineering Attacks: These attacks exploit human psychology to trick individuals into revealing sensitive information or downloading malicious software. These attacks are increasingly sophisticated, using AI to personalize attacks and evade detection.
-
Insider Threats: Malicious or negligent insiders can cause significant damage to an organization’s security posture. This includes employees who intentionally or unintentionally leak sensitive data, compromise systems, or install malicious software.
-
Lack of Security Awareness Training: Many organizations lack comprehensive security awareness training programs for their employees, leaving them vulnerable to phishing attacks and other social engineering techniques.
Addressing the human element requires a comprehensive approach, including robust security awareness training, regular security assessments, and the implementation of strong access control policies. Organizations should invest in employee training programs that educate employees about phishing attacks, social engineering techniques, and secure password practices. Furthermore, regular security awareness campaigns can help reinforce good security practices and improve overall security posture.
In conclusion, the cybersecurity landscape is dynamic and ever-evolving. The five trends discussed above highlight the critical challenges organizations and individuals face in today’s interconnected world. Proactive measures, including robust security architectures, continuous monitoring, employee training, and a strong understanding of emerging threats, are crucial for mitigating risks and protecting against increasingly sophisticated cyberattacks. Ignoring these trends is not an option; it’s a recipe for disaster. Staying informed, adapting strategies, and investing in cybersecurity are no longer luxuries; they are essential for survival in the digital age.
Closure
Thus, we hope this article has provided valuable insights into Critical Cybersecurity Threats: 5 Powerful Trends to Master. We hope you find this article informative and beneficial. See you in our next article!
google.com







